Enterprise Authentication Platform for Growing B2B Companies
Build authentication infrastructure that scales from startup to enterprise without compromising on security or compliance requirements.

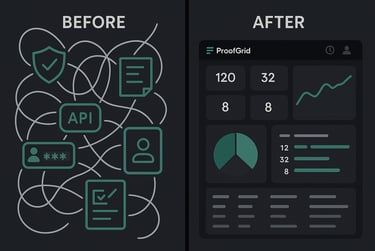
Why Most Authentication Solutions Fail Growing Companies
Growing B2B companies face a critical challenge: consumer-focused authentication tools like basic login forms work for MVPs, but enterprise customers demand comprehensive audit trails, SSO integration, and compliance-ready infrastructure.
The traditional path forces companies to choose between rapid development and enterprise readiness. This creates technical debt that becomes expensive to fix when enterprise deals depend on proper authentication infrastructure.
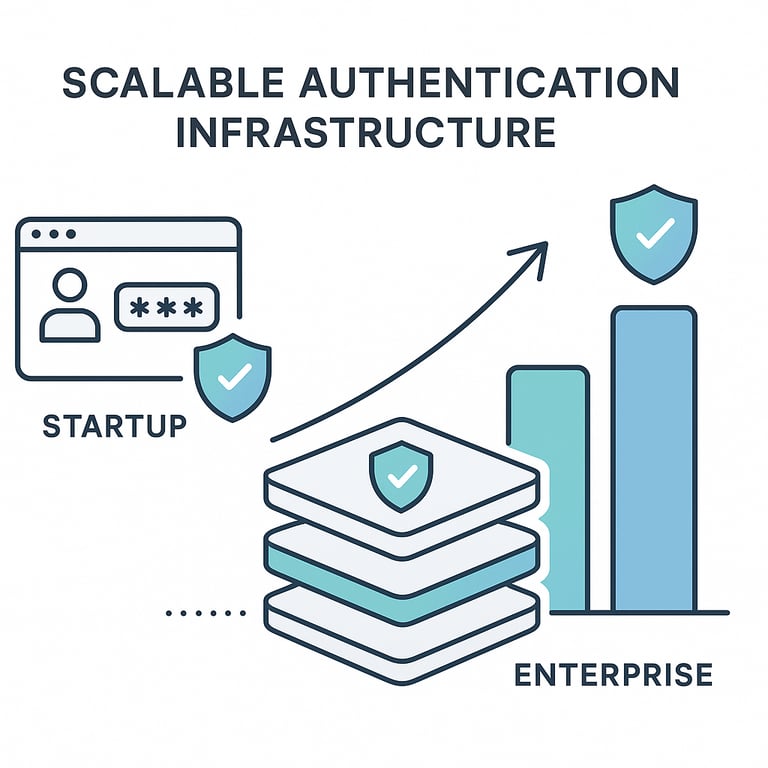
The problem: Retrofitting compliance and enterprise features typically takes 3-6 months and requires integrating multiple tools that weren't designed to work together.
Did you know?
68% of enterprise deals stall on security and compliance requirements
Average time to retrofit compliance: 6-12 months
Cost of failed enterprise deals due to authentication gaps: $200K+ per opportunity
What Enterprise Authentication Actually Means
Enterprise authentication isn't just about usernames and passwords. It's about creating systems that enterprise buyers trust and compliance teams accept.
Core Requirements That Matter:
Comprehensive Audit Trails: Every authentication event logged with full context (user, IP, device, timestamp)
Enterprise SSO Integration: OAuth 2.0 and SAML connections to corporate identity providers
Role-Based Access Controls: Granular permissions that align with organizational structure
Session Management: Configurable timeouts, concurrent session limits, geographic restrictions
API Authentication: Secure key management and rate limiting for programmatic access
Industry-Specific Needs:
Healthcare: HIPAA-compliant user identification and access logging
Financial Services: Multi-factor authentication for privileged access, audit trail retention
B2B SaaS: Multi-tenant isolation, customer-specific SSO, usage tracking integration
Authentication Architecture Patterns
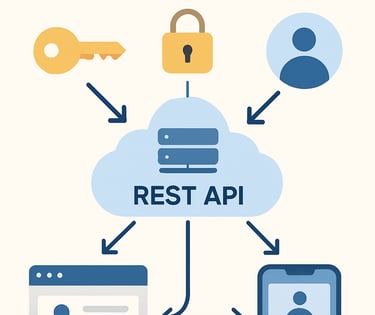
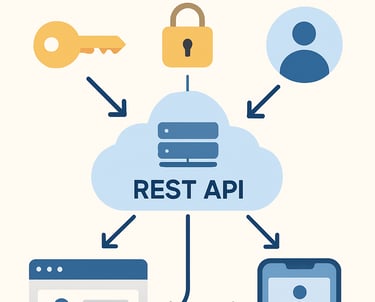
API-First Design
ProofGrid provides REST APIs for all authentication functions, allowing clean integration with existing applications without requiring specific frameworks or frontend libraries.
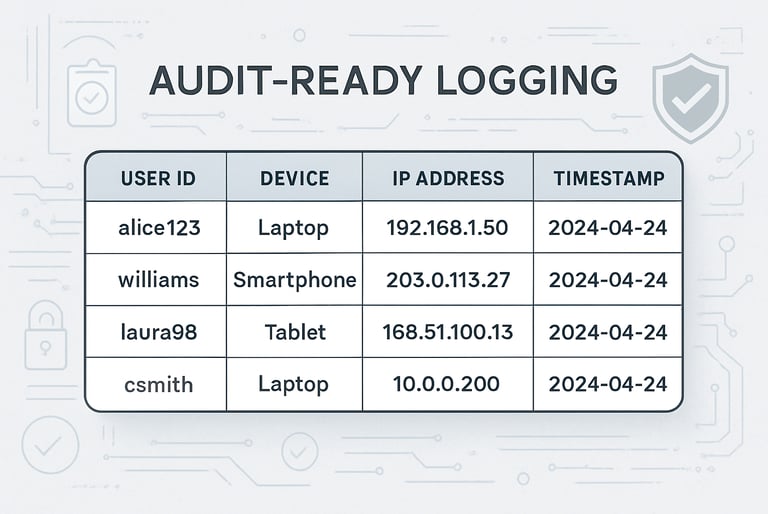
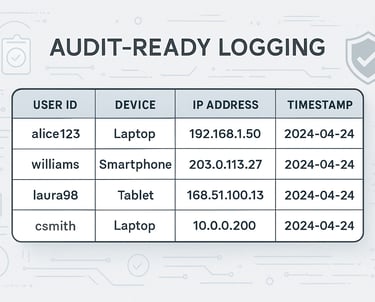
Audit-Ready Logging
Every authentication event generates structured logs designed for compliance queries. Logs include user context, device information, IP addresses, and timestamps in searchable formats.
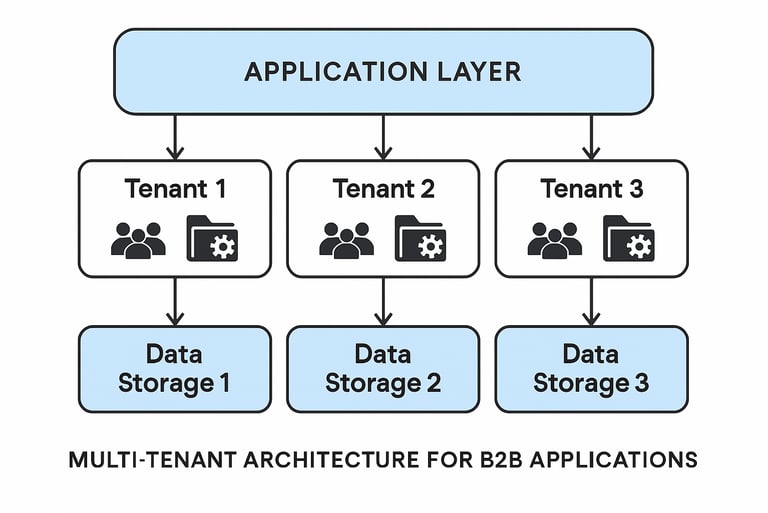
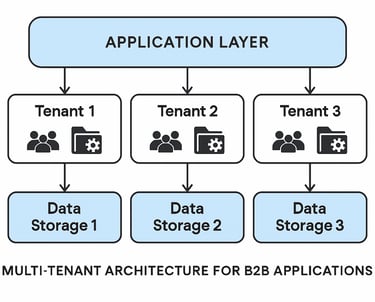
Multi-Tenant Architecture
Built for B2B applications serving multiple customers, with proper data isolation and customer-specific configuration options.
Implementation Approaches: Build vs Buy vs ProofGrid
Building Authentication In-House
Timeline: 6-12 months for basic enterprise features
Team: 2-3 senior developers plus security expertise
Ongoing: Dedicated maintenance and security updates
Risk: Security vulnerabilities, compliance gaps
Traditional Tools + Compliance Integration
ProofGrid Integrated Approach
Timeline: 3-6 months for Auth0/Clerk + Vanta/similar integration
Team: Developers plus integration specialists
Ongoing: Multiple vendor relationships, custom integration maintenance
Risk: Integration failures, vendor coordination complexity
Timeline: 1-2 weeks for standard implementation
Team: Existing development team
Ongoing: Vendor-managed updates and compliance features
Risk: Single vendor dependency
Security and Compliance Features
Security Controls:
Rate limiting and IP restrictions to prevent abuse
Secure session management with configurable policies
API key management with rotation and expiration
Multi-factor authentication options (SMS, TOTP)
Audit and Compliance:
Comprehensive authentication event logging
Failed login attempt tracking and analysis
User activity trails for security reviews
Log retention policies for regulatory requirements
Integration Capabilities:
OAuth 2.0 and SAML enterprise SSO
Webhook support for real-time event processing
REST APIs for custom integration requirements
Standard authentication protocols for compatibility
Professional Implementation Services
The Algorithm Implementation Expertise: Our implementation team brings 50+ years of combined experience building authentication systems for healthcare, fintech, and B2B applications.
Implementation Services Available:
Authentication architecture planning and design
Enterprise SSO integration and testing
Compliance requirement analysis and setup
Migration from existing authentication systems
Security review and best practices consultation
Ongoing Support:
Technical support for ProofGrid platform issues
Implementation guidance for complex requirements
Security updates and compliance monitoring
Performance optimization as applications scale
Compliance
Authentication platform with audit logging capabilities. A product by The Algorithm.
Security
Integration
© 2025 The Algorithm. All rights reserved.
Disclaimer: ProofGrid provides authentication tools that can support HIPAA/ SOC 2 compliance efforts. This information is for educational purposes only and does not constitute legal or compliance advice. Organizations remain responsible for their own HIPAA/ SOC 2 compliance and should consult with qualified compliance professionals.
